How To: Cripple Websites with DDoS Attacks or Auto-Hacking Botnets
WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.First, U.S. Senator Joe Lieberman swayed Amazon's decision to stop hosting WikiLeaks. Then, Tableau Software removed graphs from the website. After that, the company who owned the wikileaks.org name severed their relationship with Julian Assange (pictured below), the torchbearer of WikiLeaks. Then, PayPal restricted their account, hackers disrupted access to the website via DDoS attacks, MasterCard killed payments and Assange was arrested on sexual assault charges.But somehow, WikiLeaks lives on, through the heart and soul of those out for the truth. And there are now over 500 mirror websites out there containing the U.S. diplomatic cables published by WikiLeaks, which started this whole imbroglio. And with the last attack against the whistleblower website from MasterCard, angry "hactivists" are fighting back.A group of anonymous online hactivists (hacker activists) have initiated Operation: Payback, a call of action against those companies aimed to shut WikiLeaks down. These hactivists released a series of DDoS attacks against MasterCard's website, a similar tactic used to bring down WikiLeaks in the past few weeks.
Find WikiLeaksFirstly, if you want to see WikiLeaks for yourself, here are a couple places to go to:http://wikileaks.at/http://wikileaks.ch/http://wikileaks.de/http://wikileaks.fi/http://wikileaks.is/http://wikileaks.nl/http://wikileaks.no/http://wikileaks.ch/mirrors.html
What Are DDoS Attacks?If you're not sure what DDoS is, it means distributed denial-of-service, and is an attempt to make a computer resources unavailable to the intended users. To better explain, here's how Jarmo Mölsä from the National Defence College in Helsinki, Finland describes it in his article from the Journal of Computer Security— Mitigating denial of service attacks: A tutorial:A DoS attack can be carried out either as a flooding or a logic attack. A flood- ing DoS attack is based on brute force. Real-looking but unnecessary data is sent as much as possible to a victim. As a result, network bandwidth is wasted, disk space is filled with unnecessary data (e.g., spam E-mail, junk ftp data, intentional error messages), fixed size data structures inside host software are filled with bogus infor- mation, or processing power is spent for unuseful purposes. To amplify the effects, DoS attacks can be run in a coordinated fashion from several sources at the same time (Distributed DoS, DDoS). A logic DoS attack is based on an intelligent exploitation of vulnerabilities in the target. For example, a skillfully constructed fragmented IP datagram may crash a system due to a serious fault in the operating system (OS) software. Another example of a logic attack is to exploit missing authentication requirements by injecting bogus routing information to prevent traffic from reaching the victim's network.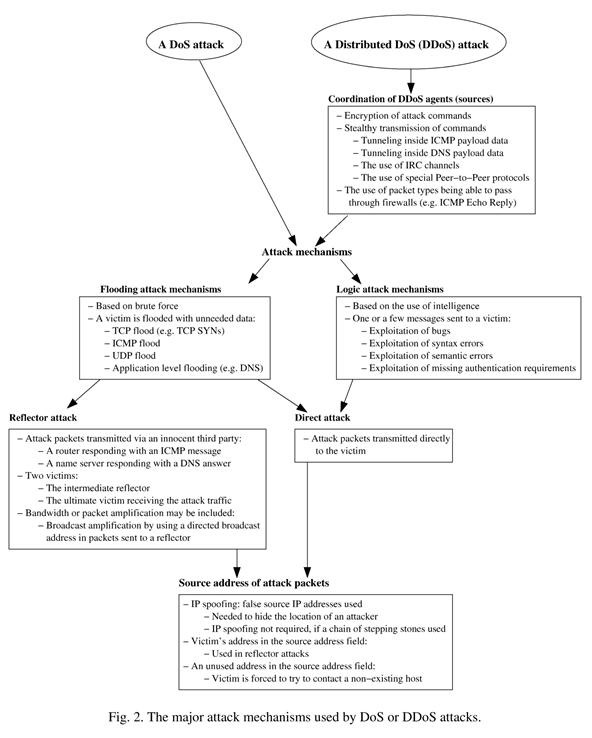
How Do You Initiate DDoS Attacks?If you want to learn how to join the fight and become an anonymous hacktivist, Mölsä's tutorial can help you initiate DoS and DDoS attacks, as well as protect your sites against them.This tutorial describes what Denial of Service (DoS) attacks are, how they can be carried out in IP networks, and how one can defend against them. Distributed DoS (DDoS) attacks are included here as a subset of DoS attacks. A DoS attack has two phases: a deployment and an attack phase. A DoS program must first be deployed on one or more compromised hosts before an attack is possible. Mitigation of DoS attacks requires thus defense mechanisms for both phases. Completely reliable protection against DoS attacks is, however, not possible. There will always be vulnerable hosts in the Internet, and many attack mechanisms are based on ordinary use of protocols. Defense in depth is thus needed to mitigate the effect of DoS attacks. This paper describes shortly many defense mechanisms proposed in the literature. The goal is not to implement all possible defenses. Instead, one should optimize the trade-off between security costs and acquired benefits in handling the most important risks. Mitigation of DoS attacks is thus closely related to risk management.Download the PDF of Mitigating denial of service attacks: A tutorial.
Disrupting Systems with Auto-hacking BotnetsPrakash published a great how-to article at Learn Hacking, about the basics of botnets and how to cripple online systems with them. Below is the complete tutorial.
Botnet Hacking TutorialIn addition to Rxbot 7.6 modded in this tutorial, you can also use another good source. It is rx-asn-2-re-worked v3 is a stable mod of rxbot and it is 100% functional and not crippled. If you want to download it, you can below:rx-asn-2-re-worked v3Q: What is a botnet?A: A botnet is where you send a trojan to someone and when they open it a "bot" joins your channel on IRC(secretly, they don't know this)Once done the computer is now referred to as a "zombie". Depending on the source you used, the bot can do several things. I myself have helped write one of the most advanced and secure bot sources out there. (Off topic) But once again depending on the source you can: Keylog their computer, take picutes of their screen, turn on their webcam and take pics/movies, harvest cdkeys and game keys or even cracks, passwords, aim screen names, emails, you can also spam, flood, DDoS, ping, packet, yada yada, some have built in md5 crackers, and clone functions to spamm other irc channels and overrun a channel and even perform IRC "Takeovers".Once again depending on the bot it may be able to kill other fellow competeter bots. Or even kill AV/FW apon startup. Add itself to registry. Open sites. Open commands. Cmd, notepad, html. Anything is possible!Theres the infected computers "bots" the attacker, the server, and the victim.Quote:While the term "botnet" can be used to refer to any group of bots, such as IRC bots, the word is generally used to refer to a collection of compromised machines running programs, usually referred to as worms, Trojan horses, or backdoors, under a common command and control infrastructure. A botnet's originator (aka "bot herder") can control the group remotely, usually through a means such as IRC, and usually for nefarious purposes. Individual programs manifest as IRC "bots". Often the command and control takes place via an IRC server or a specific channel on a public IRC network. A bot typically runs hidden, and complies with the RFC 1459 (IRC) standard. Generally, the perpetrator of the botnet has compromised a series of systems using various tools (exploits, buffer overflows, as well as others; see also RPC). Newer bots can automatically scan their environment and propagate themselves using vulnerabilities and weak passwords. Generally, the more vulnerabilities a bot can scan and propagate through, the more valuable it becomes to a botnet controller community.Suspects in the case used the Randex worm to establish a 30,000 strong botnet used to carry out "low profile DDoS attacks" and steal the CD keys for games, he explained. "They had a huge weapon and didn't use as much as they could have done," Santorelli told El Reg. "The main damage caused in the case is down to the cost of cleaning up infected PCs."Botnets are being used for Google Adword click fraud, according to security watchers.Now enough with all the quotes. As you can see, you can do anything with a botnet. Anything is possible. This is my bot and tutorial. You can host your bots on irc on a public server but I would recommend a private, password protected server. I will setup bots for people if they have something to offer.Ignore anything about using the server editor but this tutorial show how to make an irc channel and spread bots:Download the tutorialIf you want to see the rest of the tutorial, including steps on setting up the C++ Compiler in Microsoft Visual, configuring the compiler, configuring and building the bot, and executing:Click through to see the rest of this hacking tutorial.References: TIME, TechPluto, Los Angeles Times, News.com.au
Google announced Android Auto at Google I/O in 2014, but it took another year before you could actually get it in a car. Android Auto is now supported by various auto manufacturers and makers of third-party multimedia head units. The screens come in different shapes and sizes, and the hardware buttons vary.
Google Rolls Out Wireless Android Auto, but Almost No One Can
Got an Itch? Let Your Chair Do the Scratching - Gadget Hacks
There are multiple ways you have stored animated GIFs in the Photos app on your iPhone; either you have downloaded your favourite GIFs from a website, or you may have received such files via email or a friend of yours may have sent you one. In any case, you can send that animated GIF with the help of Messages app on your iPhone. Step #1.
Send & Receive Animated GIFs in Messages on iPhone
osxdaily.com/2013/07/25/send-receive-animated-gifs-iphone/
Send & Receive Animated GIFs in Messages on iPhone. A fun little-known feature of Messages for iOS is that it supports animated gifs, meaning you can send and receive those quirky moving web graphics that were so popular in 1996 and are currently enjoying a resurgence on the web.
How To Send Animated Gifs In Text Messages For Iphone
WiFi Prank: Use the iOS Exploit to Keep iPhone Users Off the Internet How To: Automatically Connect to Free Wi-Fi Hotspots (That Are Actually Free) on Your Samsung Galaxy Note 2 How To: Find & Share Local Wi-Fi Passwords for Free Internet Everywhere You Go
See Who's Using Your Wi-Fi & Boot Them Off with Your Android
Click Saved Logins… and the Password Manager will open. To see the passwords you have saved, click Show Passwords. When you close the window, your passwords will be automatically hidden. Use the search box to find a particular website or username. Click the X in the search bar to clear your search and see the full list again.
How to See Saved Passwords in Firefox: 10 Steps - wikiHow
Picking up an Android device for the very first time? Don't worry, we've got you covered! Here's out brief guide on how to navigate through your Android.KEEP IN MIND: Not all Android phones are
How to Move Home Screen Panels on an Android Phone - dummies
Color Grab is the ultimate on-the-go color tool. Pick, capture and recognize colors simply by pointing the camera. Leading and worldwide used by designers, artists, professionals, developers and color-blinds.
SwatchMatic: Capture & Identify Colors via Your Android's Camera
Apple has just released the iOS 8.3 beta 3 to its community of registered third-party developers and the update is now available for download. iOS 8.3 beta 3 has been made available for all devices that run iOS 8.
Hack Phone App Store iPhone / News: iOS 11.2 Beta 4 Released
Dec 20, 2018 · On October 8th, Apple rolled out iOS 12.0.1 with a few bug fixes. For example, iOS 12.0.1 included a fix where some iPhone XS devices had a problem charging immediately after begin connected to a
How to Fix iPhone iPad Screenshot Not Working on iOS 11/12
Best Google Assistant Tricks You Should Try 1. Select Your Favorite Google Assistant Voice. We all know that Google Assistant comes with a female voice with an American accent. However, if you don't like it you can change its voice as now Google Assistant supports multiple voices which include both men and women voices with different accents.
According to Gadget Hacks, if you're on a plan where you pay a monthly amount to cover the cost of say, and iPhone X, you should be eligible for an upgrade in a month. That's assuming you
Find Out If You're Eligible for an iPhone 5 Upgrade
Pandora's dominance. Image via Statista. While Pandora has consistently rolled out new updates that improve their application, making it increasingly more popular as they add labels, artists, and countries in which the service operates, there's one important feature that they have persistently neglected to touch—music controls in the notification shade.
The Fastest Way to Access the Notification Tray in Full
Android Enterprise provides additional management options and privacy when people use their Android devices for work. Intune helps you deploy apps and settings to Android work profile devices to make sure work and personal information are separate. All apps you install on Android work profile devices come from the Managed Google Play store.
Use This App To SUPER SMOOTH Your Android Device - youtube.com
0 comments:
Post a Comment