How To: Transfer Your Authy Account to a New Phone
One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.With Authy, you don't have to worry about losing access to important online accounts just because your phone gets lost, broken, or stolen. You can either transfer the access from one phone to another or keep your account accessible on two devices, so it is even easier to access your tokens. Both options have similar procedures, only differing by one step, which I'll outline belowDon't Miss: The 5 Best Two-Factor Authentication Apps for iPhone & Android
Step 1: Download Authy on the New PhoneObviously, you need Authy on the new phone to get started. Head over to the Play Store or App Store and download Authy.Install Authy: Android (free) | iOS (free)
Step 2: Enable Multi-DeviceTo transfer access, you need to enable Multi-Device, a feature which is disabled by default. On your old phone, open Authy and select "Settings" (on iOS) or the three vertical dots then "Settings" (on Android). The next page looks different depending on which operating system your device uses.For iOS, select the "Devices" tab located at the bottom of your screen. For Android, you'll find the same tab near the top of the screen. Once under the tab, select "Allow Multi-device" to enable the toggle.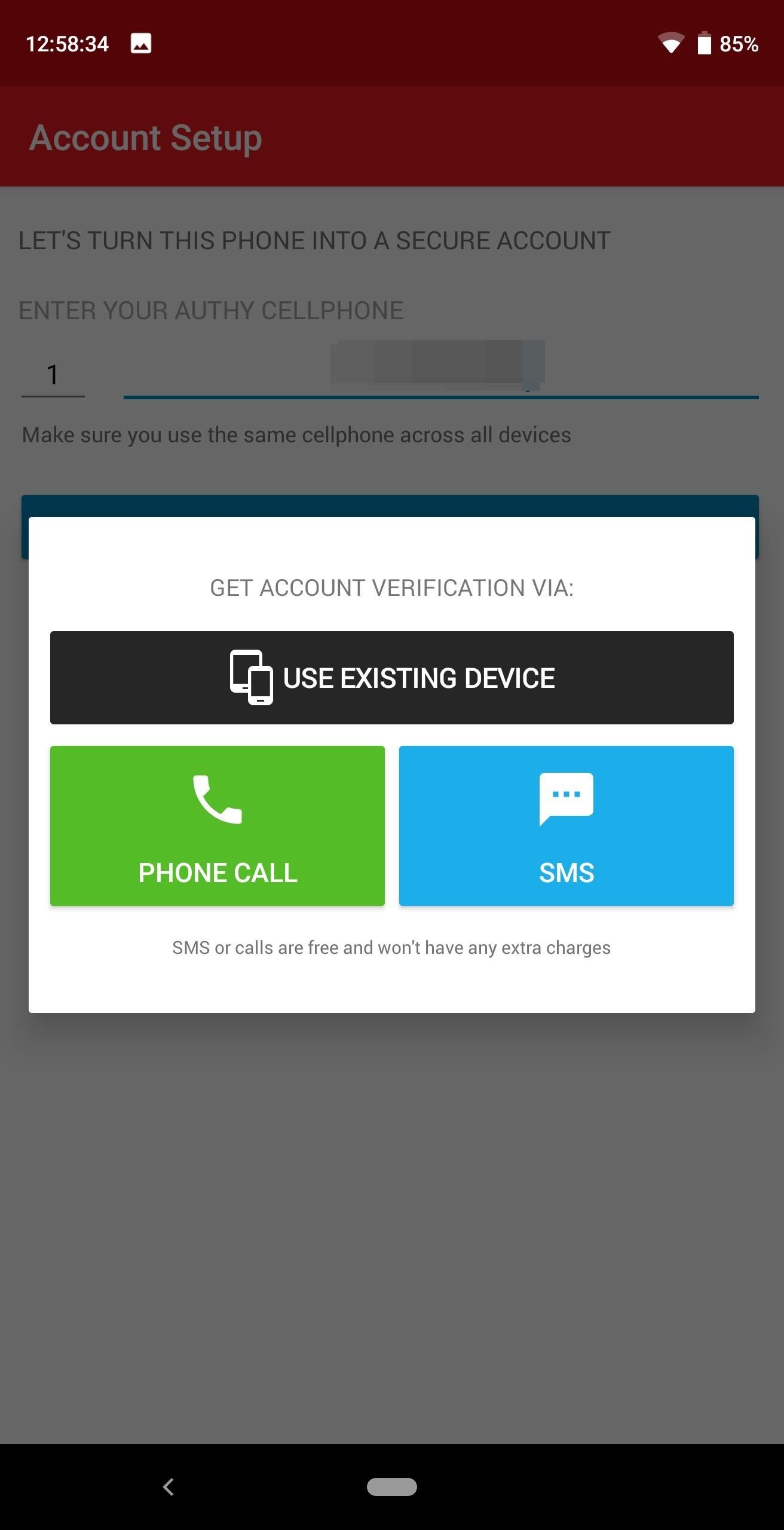
Step 3: Transfer AccessOn your new phone, when you open Authy, a page will appear asking for your phone number. Authy uses your phone number as a way to store your account, making it easier to retrieve. Once inputted, a new prompt will appear asking you to verify your account in one of three ways: using your old device, by phone, or by SMS. Since using an existing phone is both the easiest and safest method, we will start with that one. Select "Use existing device" to reveal a new prompt asking you to wait for approval. On your old phone, a notification will appear asking you to approve the new device. Select "Accept," which prompts a new popup asking you to input "Yes" (on iOS) or "OK" (on Android). Input the text and select "OK," and after a few seconds, your new device will have access to your account. If you don't have the old phone (because it's broken or stolen), you can still use "SMS" or "Phone call" to input the code. Choosing "SMS" will have the system send you a text message with your code, which you input in the prompted area. For "Phone call," Authy will call your phone number and read off the code you need to enter. Once the code is correctly entered, you can see all your accounts.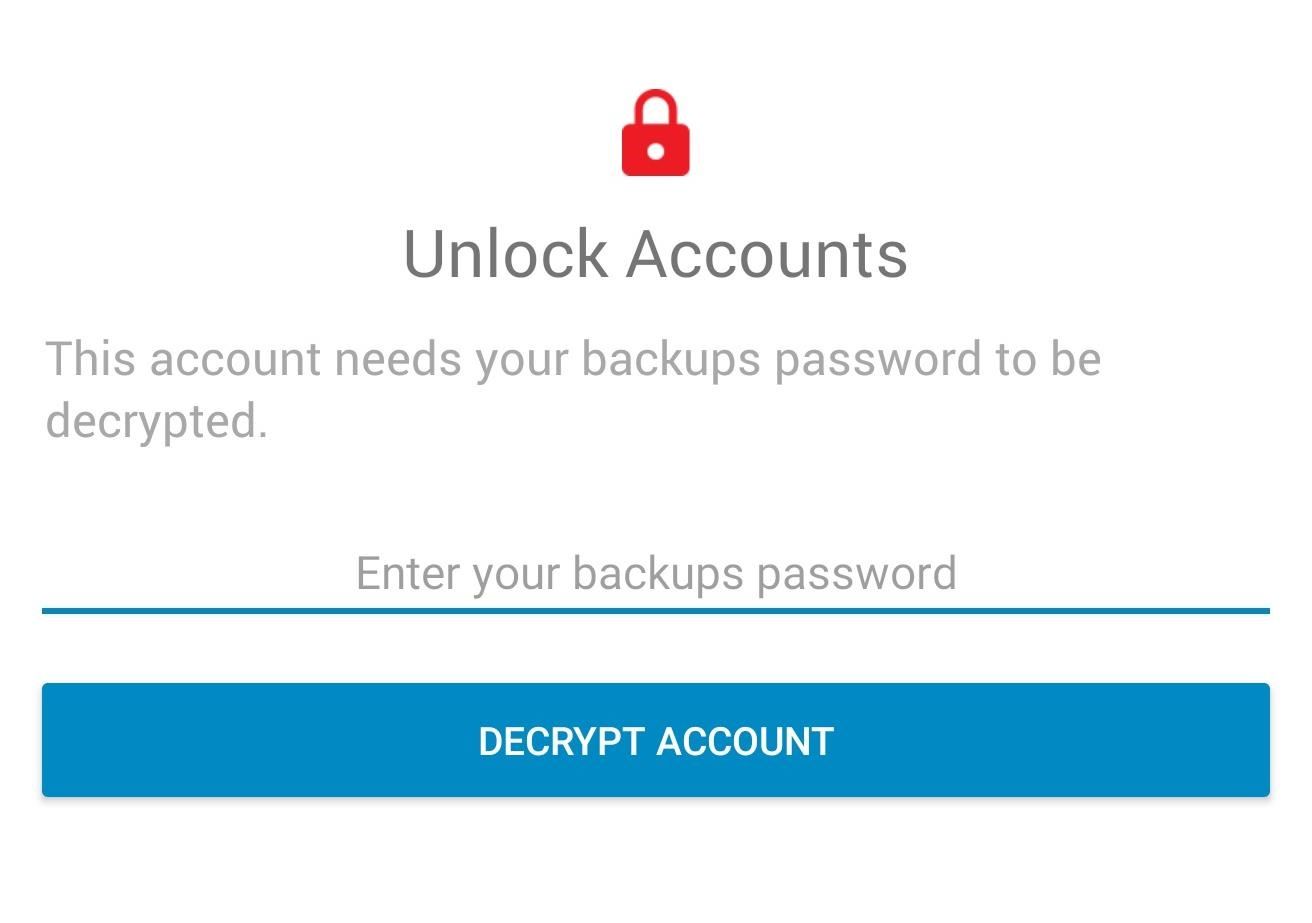
Step 4: Unlock Your DatabaseYou may have noticed that all your accounts have a small red padlock next to their name. This icon indicates that these accounts are encrypted and require a passcode to be entered before you can access them. Select an account to bring up the "Decrypt Accounts" page. Input your password (the one you created when you first signed up for Authy) and select the button.Once done correctly, you will no longer see the red padlock and you'll be able to see each token for your accounts.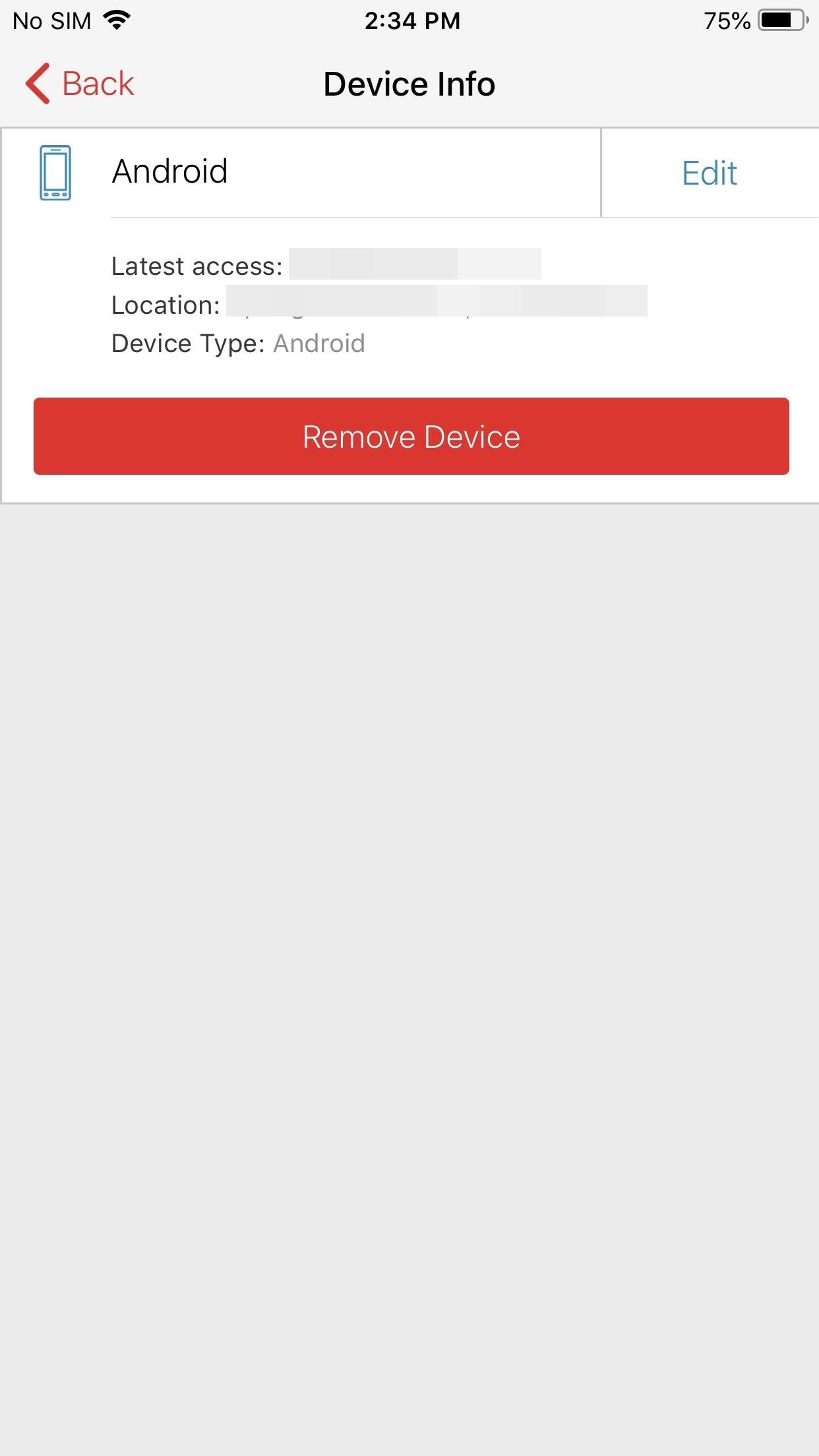
Step 5: Protect Your AccountNow that you have successfully transferred your accounts, let us re-establish protection. First, whether you are getting rid of your old phone or plan to keep it, you'll want to make sure someone else can't access your account using just your password.Since spoofing phone numbers is possible, you need to prevent a potential hacker from also adding their device to the list of connected devices. Therefore, you should turn off "Allow multi-device" (which you enabled in Step 2). By disabling this feature, a hacker won't be able to transfer access to their device.Second, if you plan to sell your old phone, or it was lost or stolen, you should remove its access so that someone using those devices can't access your tokens. Enter "Settings," and under "Devices," select a device under the grouping Other Connected Devices. Tap the "Remove Device" button and select "Yes" on the popup. Now that access it removed, a few things happen. Any Authy-powered tokens (ones which use Authy's push notifications to send tokens) will no longer work on the new device. Backup and sync will also stop working, preventing any permanent changes to your tokens. The removed device will also not be able to add new tokens or authorize new devices.You should be aware that it won't block access to tokens not powered by Authy (which will probably be most accounts), so we strongly recommend using a password manager on those accounts to strengthen your other layer of defense.Don't Miss: How To Set Up Two-Factor Authentication for Your Accounts Using Authy & Other 2FA AppsFollow Gadget Hacks on Facebook, Twitter, YouTube, and Flipboard Follow WonderHowTo on Facebook, Twitter, Pinterest, and Flipboard
Cover image and screenshots by Jon Knight/Gadget Hacks
This quick guide details how to customize the Galaxy S8 notification bar. Allowing you easy access to your most used settings or features, without fumbling through the settings menu. These same
Change notification and action settings in Windows 10
How To: Automatically Mute Media Playback When You Put Your Android in Priority Mode News: The OnePlus 6T — a Few Additions and 1 Major Subtraction News: People Are Pissed About the Lava Red OnePlus 5T October 30: The OnePlus 6T — What's Rumored & What We're Hoping For
How to Mute or Pause Music on Your HTC One by Just Waving
To make sure of this the thief rings the door bell to make sure that nobody is home, if nobody answers then they will break in. A lot of people have dogs and alarm systems which will scare off the thieves, but this alarm system combines both. To make this devise you have to buy a speaker system that connects to your door bell.
Guard Dog Burglar Alarm!: 6 Steps (with Pictures)
How to put your iPhone or iPad into DFU mode | iMore
There are tons of steps you can take to run faster, smoke the competition, and maybe even sent a new PR. 1. Nail good form. The key to running (at any speed) is to practice proper running
How to Hack a voice changing toy to make it sound even
Every Mac Is Vulnerable to the Shellshock Bash Exploit: Here's How to Patch OS X. First, the "legal" stuff. If you decided to follow these steps, and something breaks - ITPro-Blog.com can in no way be held liable.
Shellshock Bash Exploit: Patch OS X - A Geek to Go, LLC
This is why an app called Smart Launcher has been gaining popularity lately with over 10 million installs—it has an app drawer that analyzes your apps and usage data to automatically group apps into well-organized tabs. But now, the Smart Launcher developers have broken their futuristic app drawer out as a standalone product.
How to Add Smart Drawer and Get Automatic Sorting Feature On
Stop Asking Me To Cut and Paste Stuff On My Wall. 359 likes. I'll bet 96% of people won't share THIS SITE on their walls - do YOU have the courage?
How Facebook Is Using You to Annoy Your Friends (and How to
Research suggests that as many as about 40% of women and men in the US who are in their 30s and 40s have tried it at least once. Some never try it again. Some do it every now and then. As is being pointed out in this forum, however, few people engage in it frequently. However, everyone is different and if you enjoy it, then have fun!
MakeVR Lets You Create 3D Models in Virtual Reality with Real
How to Use Google toolbar to share links with friends
I'm looking into creating a python script that will kill some of the common processes within Windows such as some anti-virus processes, and cmd.exe (including explorer.exe to check if it works).
Writing Python Script « Null Byte :: WonderHowTo
0 comments:
Post a Comment